We are a charity and we needed to protect ourselves and our clients. Lanmark’s 24x7x365 XDR solution gives us the peace of mind that our systems are safe from attack.
24 x 7 Managed Cyber Security Services & Solutions in London
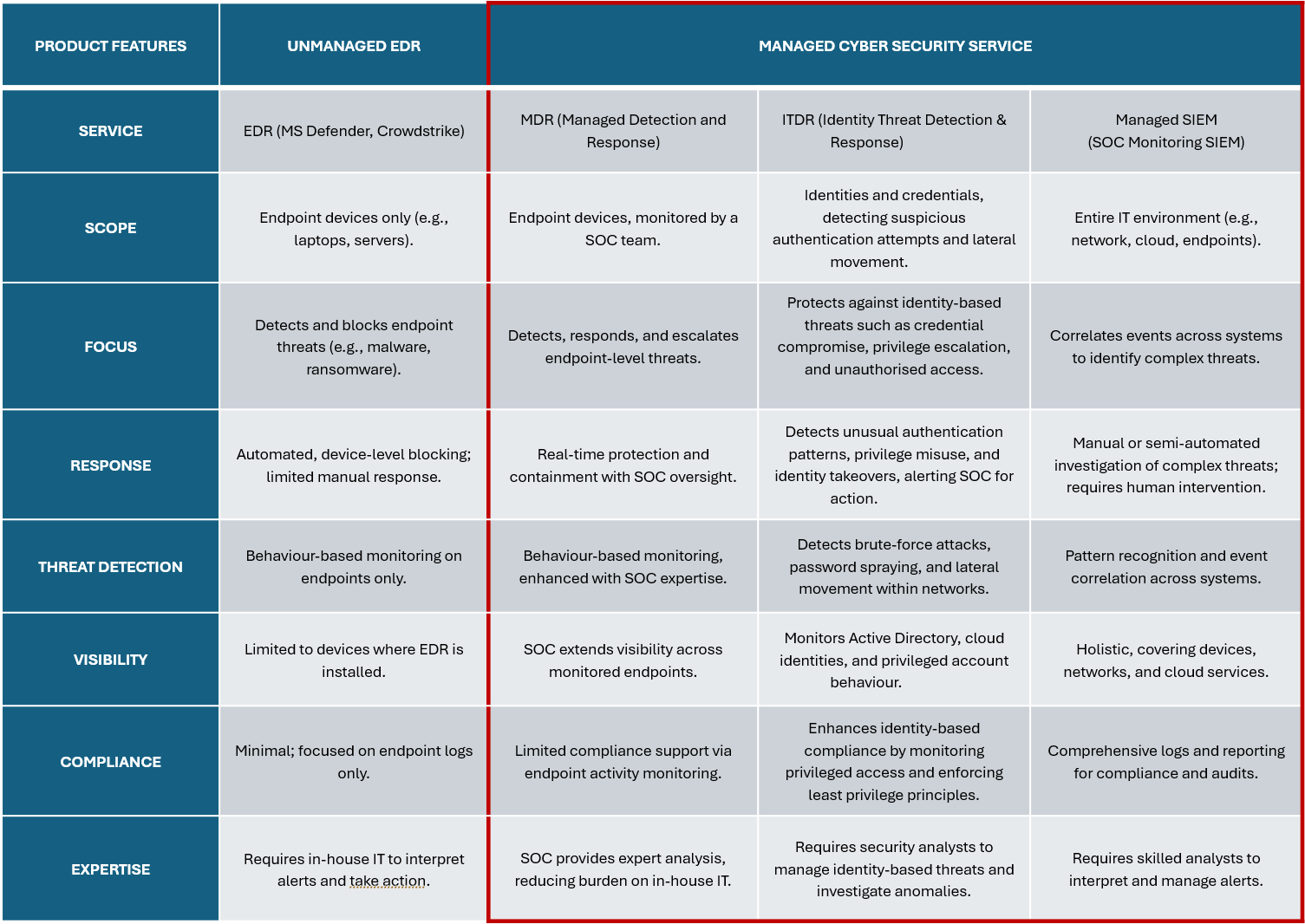
In today’s digital landscape, cyber threats are becoming increasingly sophisticated and pervasive. Attackers continuously evolve tactics, techniques, and procedures (TTPs) to bypass traditional security measures. Managed Cyber Security Services leverage cutting-edge technologies and expert analysis to effectively detect and respond to these advanced threats.
Our complete solution combines MDR-as-a-Service, ITDR-as-a-Service and SOC-as-a-Service to provide 24/7 real-time monitoring of your users, network and endpoints. This continuous visibility allows for the early detection of malicious activities and potential security incidents, minimising the dwell time of threats within your environment.
Our Security Operations Centre employs skilled cyber security professionals specialising in threat detection and incident response. These experts have the knowledge and experience to quickly assess and mitigate security incidents, reducing the impact and potential damage caused by cyber-attacks.